What are the best PHP security practices?
When working with PHP, it’s imperative to have strong security procedures. Keeping PHP and its related libraries up to date, sanitizing and validating user input to thwart SQL injection and cross-site scripting (XSS) attacks, using secure hashing algorithms for password storage, and implementing secure session management strategies are some of the basic security guidelines in PHP. Furthermore, it’s crucial to put in place appropriate access restrictions, safeguard sensitive data, and carry out regular security audits and testing. By using these techniques, risks can be reduced and PHP applications’ integrity and security are guaranteed.
Ferris Bueller’s Day Off
Time and technology are linked and ever-evolving. While using cutting-edge technologies to create a web application can take time, the process doesn’t end there. Taking a step back to evaluate potential security issues is crucial. It is crucial to safeguard your online apps from harmful attacks. Developers should put in their best effort to fix any flaws and stop future security breaches.
Due to PHP’s extensive use, many businesses use it in their everyday operations. Numerous businesses have started bounty programmes, asking security professionals to examine their apps and find crucial PHP security flaws, in order to assure the security of PHP websites. By putting these strategies into practice, you may build a strong security structure for your PHP website, protecting it from threats and hackers. To help you with the PHP security guide, we have compiled a list of ten fundamental security guidelines.
Thou shalt update PHP on a regular basis
Thou shalt upload files more securely
Thou shalt armor from SQL Injection Attacks
Thou shalt leverage HTTPs SSL Certificates
Thou shalt deploy PHP Apps on Clouds
Thou shalt investigate on Cross site request forgery XSRF/CSRF
Thou shalt always hide every files from your browser
Thou shalt involve Cross-site scripting (XSS)
Thou shalt involve Session Hijacking
Thou shalt use the right PHP infrastructure
Thou shalt update PHP on a regular basis
While you are scripting the website through WordPress, the script would run a software program that we proudly call PHP on various servers. You should also know that PHP would be interpreting your programming code in your script. This would also generate your web pages for people to view easily. In comparison to any other software, PHP  would come along in different versions. In case of newer versions, it is going to be faster as well as fewer bugs. A few scripts might not work properly. In those cases, we need to let our customers make a choice between various PHP versions. Yu should also know how to choose a recent compatible version that goes along with your scripts. The latest PHP version as of now is PHP 7.2.8. Developers consider it to be the most stable version. When you are using PHP 5.6 or below that, you may face certain constraints while upgrading all your PHP apps. You need to be aware that various scripts such as WordPress act similar to your computer programs. PHP is nothing but the Mac or Windows Operating System we use on the computer system. You need to keep upgrading it to get the best out of it. You may require to update the code and make changes to some functional logics such as password hashing. Some tools such as PHP 7 MAR or PHP 7 Compatibility Checker can check the code deprecation too. While you use PHPStorm, you can leverage PHP 7 Compatibility Inspection to know which code is being troublesome. You have to know how to secure PHP development websites from hackers. This would help you to build your products in a safe and secure manner. Your PHP developer is going to benefit from the way you build the products in a user-friendly manner. This is going to help you sustain the PHP product in the long run.
would come along in different versions. In case of newer versions, it is going to be faster as well as fewer bugs. A few scripts might not work properly. In those cases, we need to let our customers make a choice between various PHP versions. Yu should also know how to choose a recent compatible version that goes along with your scripts. The latest PHP version as of now is PHP 7.2.8. Developers consider it to be the most stable version. When you are using PHP 5.6 or below that, you may face certain constraints while upgrading all your PHP apps. You need to be aware that various scripts such as WordPress act similar to your computer programs. PHP is nothing but the Mac or Windows Operating System we use on the computer system. You need to keep upgrading it to get the best out of it. You may require to update the code and make changes to some functional logics such as password hashing. Some tools such as PHP 7 MAR or PHP 7 Compatibility Checker can check the code deprecation too. While you use PHPStorm, you can leverage PHP 7 Compatibility Inspection to know which code is being troublesome. You have to know how to secure PHP development websites from hackers. This would help you to build your products in a safe and secure manner. Your PHP developer is going to benefit from the way you build the products in a user-friendly manner. This is going to help you sustain the PHP product in the long run.
Thou shalt upload files more securely
Uploading a file is very important for any user data processing app. Sometimes, these files can also be used for XSS attacks. Do not forget to make use of the POST request while using the form. Always declare the property “enctype=”multipart/form-data” while using the <form> tag. Then validate the file type with the help of finfo class. Developers are free to create their own rules to securely conduct file validation. Many frameworks such as Symfony, Laravel and codeigniter can aid you in this pursuit with their customized methods to achieve this feat.
You have to declare the basename() and UPLOAD_ERR to prevent any attacks on your directory. You need to validate your file size and rename it before you store your uploaded files in different private locations. You also need to strengthen your application security through it.
Thou shalt armour against SQL Injection Attacks
SQL Injection (SQLi) is nothing but a kind of injection attack where you can execute every malicious SQL statement. These statements would handle every database server behind a single web application. Attackers can make use of vulnerabilities involving SQL Injection to handle security measures. They take care of factors like authorization and authentication of every web page or web app. They can retrieve any content present in the entire SQL database. They can also leverage SQL Injection if they are willing to add, delete or modify any existing records in their database.
The SQL injection would be the most commonly known problem in PHP scripting. Your whole application could get compromised with a single query. When there is an SQL injection attack, the attacker would try to make changes to the data you pass through queries. The $username would contain rendered data. This can damage your database and let you delete the entire database within a few seconds. The best solution to avoid this is to make use of prepared statements. PDO would allow you to secure your data.
Thou shalt leverage HTTPs SSL Certificates
Every modern web browser such as Google Chrome, Firefox and Opera would recommend you to use HTTPS protocol while you handle your web applications. An SSL certificate binds a cryptographic public key to a website. HTTPs would offer more security and encryption facilities for untrustable websites. Include HTTPs when you install an SSL certificate into the website. This would power up your web apps while dealing with XSS attacks. This can in turn prevent every hacker from reading the data you have transported data with the help of codes. HTTPS would play a great role in providing privacy and security by reducing the traffic visibility to people who are monitoring them.
Thou shalt deploy PHP Apps on Clouds
PHP Development has got little to do with Cloud Hosting. You should not be the one confusing both the terminologies altogether. If you are a PHP Developer, you should understand  where you need to adhere to your user requirements. You should be a flexible individual. You should build an extraordinary solution that would cater to all the demands of your audience. If you are using the system, you need to make sure that everything goes as per the customer requirements. With PHP Development, you are all set to build a dashing solution. Before that, you need to know more about hosting, even though hosting would be the final destination of your web app journey. With this, you would always be capable of creating your project on different PHP servers. You can deploy the app on live servers with cloud, shared or dedicated hosting facilities. There are faster cloud hosting tools like AWS. AWS is comparatively safe and secure than any other platform. You get to prevent DDOS, phishing attacks and Brute force in your web apps. You can deploy any PHP app on Oracle or Google cloud. These are the things you need to ensure before deploying any PHP app:
where you need to adhere to your user requirements. You should be a flexible individual. You should build an extraordinary solution that would cater to all the demands of your audience. If you are using the system, you need to make sure that everything goes as per the customer requirements. With PHP Development, you are all set to build a dashing solution. Before that, you need to know more about hosting, even though hosting would be the final destination of your web app journey. With this, you would always be capable of creating your project on different PHP servers. You can deploy the app on live servers with cloud, shared or dedicated hosting facilities. There are faster cloud hosting tools like AWS. AWS is comparatively safe and secure than any other platform. You get to prevent DDOS, phishing attacks and Brute force in your web apps. You can deploy any PHP app on Oracle or Google cloud. These are the things you need to ensure before deploying any PHP app:
- The Google Cloud project’s owner should create their App Engine application.
- Make sure that the user account contains all the required privileges.
When you are going to use PHP servers, you should ensure that it is safe. You should be aware of PHP security issues. If you know how to secure PHP website from hackers, you would be able to rock the market. This is going to bring a great change in the perspective of your customers. Hence it would be a wise choice to deploy your PHP Apps on cloud to ensure that the process is entirely safe and secured elsewhere.
Thou shalt investigate on Cross site request forgery XSRF/CSRF
Cross-Site Request Forgery (CSRF) would force the end user to handle unrelated actions on their authenticated web app. When there is a potential CSRF attack, the attacker would allow the victim user to let any action take place unintentionally. This might involve changing the account’s email id, to change the password or to transfer the funds. It depends on the action’s nature if the attacker is able to control the user’s account entirely. If the user who gets compromised within the app has complete privileges, the attacker would get the horns on his hand. The app’s functionality and data would get transferred to the other user. CSRF attacks would target more state-changing requests that are not subjected to any data theft. The attacker would not see any response when it comes to the forged request. With PHP, the user has to make sure that this does not happen.
Thou shalt always hide every files from your browser
With regards to PHP Development, cross-Site Request Forgery (CSRF) would force the end user to handle unrelated actions on their authenticated web app. When there is a potential CSRF attack, the attacker would allow the victim user to let any action take place unintentionally. This might involve changing the account’s email id, to change the password or to transfer the funds. It depends on the action’s nature if the attacker is able to control the user’s account entirely. If the user who gets compromised within the app has complete privileges, the attacker would get the horns on his hand. The app’s functionality and data would get transferred to the other user. CSRF attacks would target more state-changing requests that are not subjected to any data theft. The attacker would not see any response when it comes to the forged request. With PHP, the user has to make sure that this does not happen.
Thou shalt involve Cross-site scripting (XSS)
Cross-site Scripting (XSS) vulnerabilities can occur anywhere where you can alter your information. Using this, any user can alter the information. This would reflect directly on the website’s output. Cross-site Scripting (XSS) attacks is an injection type, in which you inject malicious scripts into more trusted and widely accepted websites. XSS attacks would occur when an attacker would make use of a web app to send malicious code. This might happen as a browser side script to another end user. Flaws allowing successful attacks are widespread. This could occur wherever a web app would use a user out that gets generated without any validation or encoding.
An attacker would make use of XSS for sending a malicious script to the user who does not suspect it. The end user’s browser would not have any way to know if he can trust the script. Then he would execute the particular script. It would be of the notion that the script arrived from a more trusted source. This would allow a malicious script to access any session tokens, cookies or any other confidential information. This would allow the attacker to rewrite the script.
Thou shalt involve Session Hijacking
Session hijacking would be a barrier in the lines of any PHP Developer. They should avoid it at any cost. According to Stack Overflow, we use the term “session” to communicate various server and browser side of things. 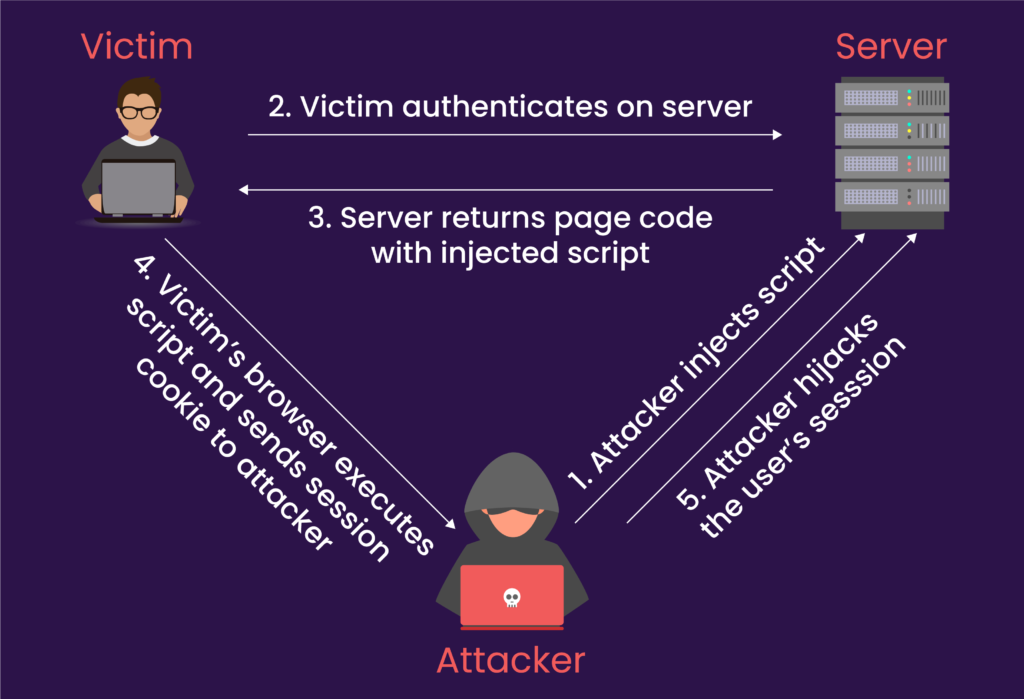 One should remember that the browser sessions connected directly to server sessions. “Session hijacking” would mean server sessions. Session hijacking is a kind of malicious web attack where the attacker would steal your session ID without your knowledge. The server would be sending the associated $_SESSION array to validate its stack storage and allow access to your application. You can expect session hijacking from XSS attack. That could also happen when someone is accessing the server’s folder where you store the session data. Always prevent session hijacking by binding different sessions to all your IP addresses. When there is any violation, make sure that you are not exposing any IDs. Ensure that you unset session storage, cookies and remove different traces. Always avoid using any serialized data that you store in a cookie. Hackers would be able to take charge of your cookies in an easy manner. That would allow you to add different variables to the scope. You should always be aware of the PHP security issues if you want to build the best product. You should take steps to rectify it effectively.
One should remember that the browser sessions connected directly to server sessions. “Session hijacking” would mean server sessions. Session hijacking is a kind of malicious web attack where the attacker would steal your session ID without your knowledge. The server would be sending the associated $_SESSION array to validate its stack storage and allow access to your application. You can expect session hijacking from XSS attack. That could also happen when someone is accessing the server’s folder where you store the session data. Always prevent session hijacking by binding different sessions to all your IP addresses. When there is any violation, make sure that you are not exposing any IDs. Ensure that you unset session storage, cookies and remove different traces. Always avoid using any serialized data that you store in a cookie. Hackers would be able to take charge of your cookies in an easy manner. That would allow you to add different variables to the scope. You should always be aware of the PHP security issues if you want to build the best product. You should take steps to rectify it effectively.
Thou shalt use the right PHP infrastructure
There might be any fixes or patches that you allow on your system using PHP Development, then they are not going to be fruitful if you are not going to set up the infrastructure properly. The infrastructure comprises different containers, tools, load balancers, cache stores, database servers and much more. If you are not going to configure them properly or when you mismanage the credentials or when the system is not upgraded, there are high chances of unauthorized users to restrict data or information exchange between different networks. Your network setup would also involve more threats. You need to set up a firewall to prevent risks.
These are the other reasons why attackers may thrive on your data on PHP:
- Unlooked upon vulnerabilities in your security
- Not adhering to any credential management strategy
- Abusing user account privileges that are provided by the company
- Neglecting the importance of encryption
Why do you need to consider Pattem Digital for your PHP requirements?
Are you looking for a PHP Web Development company? At Pattem Digital, we don’t just serve our customers. We are deeply involved with our customers and work as a team. We make sure that every customer requirement is handled, right from documentation to support. This would ensure that you are on the right track.
If you are setting out on your PHP requirements, then Pattem Digital is the right place to start. We have PHP experts who can nail it!
Let us know what your requirements are pertaining. We would underpin it with our expertise, skillset and dedication towards our commitment!